For the last days, I was working to get my ISP connection @home (Which is from KPN) working with a FortiGate firewall. Well, it was a bit of a puzzle to get this working because information about this topic is very fragmented to find. So, I want to write about what I’ve done to get this working.
What do I have?
- Internet from KPN (dutch ISP) with FTTH (Fiber-to-the-home) 200/200 Mbps
- Interactive-TV from KPN
- I do not use telephony from KPN
- Experia box V10A from KPN
- FortiGate 60F (FortiOS 6.4)
- Internal switch where I can do some vlan-stuff with
You MUST use FortiOS 6.4 for this to work. Otherwise, the DHCP-client option which is used for iTV cannot be configured as this option is only available in FortiOS 6.4.
Update 5 dec 2022: some parts of this post are updated for FortiOS 7.2.
What did I want to realize?
I do not want to use the Experia box of KPN! I want to use my own FortiGate firewall to take over all the functions of the Experia box (apart from WiFi, where I have my own access-points)
What are the topics?
The topics to build are:
- Internet-connectivity (IPv4 & IPv6)
- iTV including replay and recordings
Building Internet
My ISP-connection is delivered over fiber, which is delivered with an UTP-connection from the NTU. The UTP cable is going directly into the WAN-port of my FortiGate.
Good to know is that KPN is providing me 3 vlans in total to carry their services:
- vlan 4 = iTV
- vlan 5 = Telephony
- vlan 6 = Internet
So, first I need to create a vlan-interface for vlan 6 on the WAN-port. Because of the PPPoE overhead, the MTU of the WAN-port needs to be set to 1514 bytes, and the vlan-interface itself needs to be set to 1506 bytes.
config system interface
edit "wan1"
set mtu-override enable
set mtu 1514
next
edit "internet"
set alias "vlan6"
set estimated-upstream-bandwidth 200000
set estimated-downstream-bandwidth 200000
set role wan
set snmp-index 8
set mtu-override enable
set mtu 1506
set interface "wan1"
set vlanid 6
next
endNext, we want to create the PPPoE-Interface. We bind this PPPoE-interface to the wan1 interface.
## This config is applicable to FortiOS 6.4 ##
config system interface
edit "pppoe1"
set mode pppoe
set allowaccess ping
set type tunnel
set estimated-upstream-bandwidth 200000
set estimated-downstream-bandwidth 200000
config ipv6
set ip6-mode dhcp
set ip6-allowaccess ping
set dhcp6-prefix-delegation enable
end
set interface "internet"
next
end## This part is for FortiOS 7.2. The v6-ranges should match the range which is received from KPN ##
config system interface
edit "wan1"
set vdom "root"
set status down
set type physical
set alias "KPN"
set role wan
set mtu-override enable
set mtu 1506
next
edit "pppoe"
set vdom "root"
set mode pppoe
set allowaccess ping
set type tunnel
set alias "internet"
set role wan
config ipv6
set ip6-mode dhcp
set dhcp6-prefix-delegation enable
config dhcp6-iapd-list
edit 5
set prefix-hint 2a02:aaaa:bbbb::/48
next
end
end
set interface "wan1"
next
endNote the config ipv6 IPv6 part; this part is neccesary to get an IPv6-prefix, which is advertised by the ISP via DHCPv6 prefix-delegation or DHCPv6-PD.
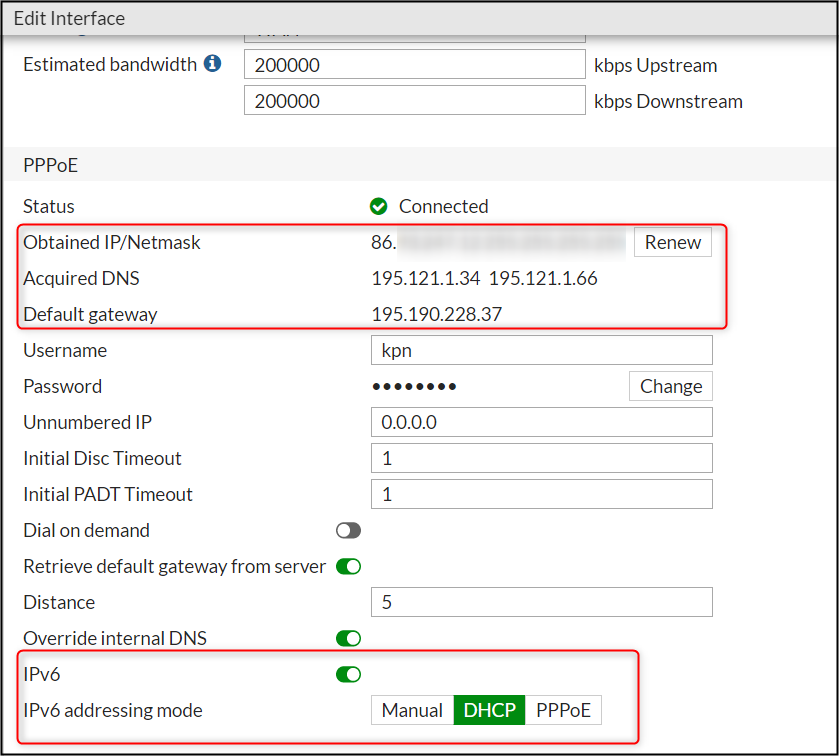
When we take a look of the PPPoE interface-part in the GUI of the FortiGate, you should see the IPv4 address which we have got from KPN.
we can also see that there is nothing visible about the DHCPv6-PD config. So, this part is only visible (and configurable) under the CLI.
If everything is okay, it should be possible to send some pings to hosts on the Internet over IPv4.
FGT60F # execute ping www.google.com
PING www.google.com (172.217.19.196): 56 data bytes
64 bytes from 172.217.19.196: icmp_seq=0 ttl=119 time=3.4 ms
64 bytes from 172.217.19.196: icmp_seq=1 ttl=119 time=3.4 ms
64 bytes from 172.217.19.196: icmp_seq=2 ttl=119 time=3.4 ms
64 bytes from 172.217.19.196: icmp_seq=3 ttl=119 time=3.4 ms
64 bytes from 172.217.19.196: icmp_seq=4 ttl=119 time=3.4 ms
--- www.google.com ping statistics ---
5 packets transmitted, 5 packets received, 0% packet loss
round-trip min/avg/max = 3.4/3.4/3.4 msIf your ping is working, then you have succesfully configured an IPv4 Internet-connection with your FortiGate. Now you can start with building your IPv4 policy-rules for your internal vlan (which is not part of this post).
At this moment, it is not possible (yet) to ping an IPv6 host on the Internet:
FGT60F # execute ping6 ipv6.google.com
connect: Network is unreachableThe ping6 is not working because there is no route for IPv6 defined. We need to do this statically. We point the IPv6 default-route to the pppoe1 interface.
config router static6
edit 1
set device "pppoe1"
next
endAfter this, you should be able to ping an IPv6 host:
FGT60F # exec ping6 ipv6.google.com
PING ipv6.google.com(2a00:1450:400e:806::200e) 56 data bytes
64 bytes from 2a00:1450:400e:806::200e: icmp_seq=1 ttl=120 time=3.71 ms
64 bytes from 2a00:1450:400e:806::200e: icmp_seq=2 ttl=120 time=3.73 ms
64 bytes from 2a00:1450:400e:806::200e: icmp_seq=3 ttl=120 time=3.66 ms
64 bytes from 2a00:1450:400e:806::200e: icmp_seq=4 ttl=120 time=3.66 ms
64 bytes from 2a00:1450:400e:806::200e: icmp_seq=5 ttl=120 time=3.68 msNow IPv6 is working to the outside world, we need to route it internally so that hosts can get an IPv6 address (Global Unicast). Therefore, we need to configure an IPv6-prefix on the inside interface of the FortiGate.
As KPN is giving you a /48 prefix, we can assign an /64 prefix to the internal network. The hosts which are internally, are getting an IPv6 address using SLAAC, which is the most easiest way to address your hosts for IPv6. Another option is to configure DHCPv6 (not part of this post).
Note that the 2a02:xxxx:xxxx:xxxx::/64 part of the config should be your IPv6 range which is allocated to you by KPN. If you don’t know this prefix, you can find this when you connect your Experia box and take a look in the web-interface.
## This part is applicable to FortiOS 6.4 ##
config system interface
edit "internal"
set ip 10.1.1.1 255.255.255.0
set allowaccess ping https ssh http fgfm
set role lan
config ipv6
set ip6-mode delegated
set ip6-allowaccess ping
set ip6-send-adv enable
set ip6-upstream-interface "pppoe1"
set ip6-subnet 2a02:xxxx:xxxx:xxxx::/64
config ip6-delegated-prefix-list
edit 1
set upstream-interface "pppoe1"
set subnet 2a02:xxxx:xxxx:xxxx::/64
next
end
end
next
end## This part is applicable to FortiOS 7.2. Mention the "5" for the prefix-iaid. This number MUST MATCH the dhcp6-iapd-list rule-index number (edit 5), which is under the pppoe logical-interface ##
edit "internal"
set vdom "root"
set ip 10.1.1.1 255.255.255.0
set allowaccess ping https ssh fabric
set type hard-switch
set role lan
config ipv6
set ip6-send-adv enable
config ip6-delegated-prefix-list
edit 1
set upstream-interface "pppoe"
set delegated-prefix-iaid 5
set subnet 2a02:aaaa:bbbb:10::/64
next
end
end
next
endWhen this config is done, you should be able to check if the IPv6-prefix is allocated to the internal interface.
FGT60F # diagnose ipv6 address list
#--- output ommitted ---
dev=25 devname=internal flag= scope=0 prefix=64 addr=2a02:xxxx:xxxx:xxxx:: preferred=171972 valid=258372 cstamp=10939 tstamp=10939
#--- output ommitted ---Note: I’ve seen that I need to restart the firewall to get this step done.
The final thing to do to get IPv6 working for your hosts, is to create a policy-rule for v6 in the FortiGate without NAT. Since NAT is not usual with IPv6, we do not enable this.
config firewall policy
edit 0
set name "outbound-internet v6"
set srcintf "internal"
set dstintf "pppoe1"
set srcaddr6 "all"
set dstaddr6 "all"
set action accept
set schedule "always"
set service "ALL"
set utm-status enable
next
endNow, as we take an internal host (I have a Win10 PC) then you can try to do an ipconfig /all to see your IPv6 addresses (you will get 2 temporary adresses).

Test your IPv6 connectivity: https://ipv6-test.com/
Building interactive-TV
See part 2.