After I got my internet connection from KPN rolling through my FortiGate, the next step was to make interactive TV (iTV) working through my FortiGate as well.
Well, it was a bit of a puzzle to get this working, because of some special settings which are needed for iTV. But when all these things are set, iTV works (almost*) perfectly through the FortiGate.
So why almost* do you think? Well, after testing for a while, it seems that I have a problem with my Internet performance when I have 2 TV receivers active. When both receivers are active, they are using for about ~7-8 Mbps of bandwidth each. So, when 2 receivers are active, I only keeps several Mbits of internet speed left…(I have a 200/200 Mbps contract, which I can easily utilize for 100% when only 1 or no receivers are active). It seems to me that the multicast stream of 2 receivers is a bit to much for my FortiGate 60F.
I decided to route the TV traffic via a dedicated router, and that worked fine! Now I can fully utilize my internet connection even when both receivers are active. In my opinion, separating TV traffic through a dedicated router is the best solution. My router is a Mikrotik RB750Gr3.
This post describes the situation where all traffic is routed through the FortiGate. The situation where I route multicast TV traffic though a dedicated MikroTik router, will be described in a later post.
What do I have?
- Internet from KPN (dutch ISP) with FTTH (Fiber-to-the-home) 200/200 Mbps
- Interactive-TV from KPN
- I do not use telephony from KPN
- Experia box V10A from KPN
- FortiGate 60F (FortiOS 6.4)
- Internal switch where I can do some vlan-stuff with
You MUST use FortiOS 6.4 for this to work. Otherwise, the DHCP-client option which is used for iTV cannot be configured as this option is only available in FortiOS 6.4.
What did I want to realize?
I do not want to use the Experia box of KPN! I want to use my own FortiGate firewall to take over all the functions of the Experia box (apart from WiFi, where I have my own access-points)
What are the topics?
The topics to build are:
- Internet-connectivity (IPv4 & IPv6) (see post part 1)
- iTV including replay and recordings (this post, part 2)
Building iTV
My ISP-connection is delivered over fiber, which is delivered with an UTP-connection from the NTU. The UTP cable is going directly into the WAN-port of my FortiGate.
Good to know is that KPN is providing me 3 vlans in total to carry their services:
- vlan 4 = iTV
- vlan 5 = Telephony (which I don’t use)
- vlan 6 = Internet
So, for iTV we are going to work with vlan 4. Let’s make up a summary about the steps I did:
- Make up vlan 4 connectivity on the wan-port of my FortiGate
- enable DHCP client (with options)
- create the neccesary routing
- configure the internal interface for the TV-receivers
- configure policy-rules
- set some global parameters
- enjoy iTV via the FortiGate 🙂
Step 1: Create vlan 4 connectivity
First, I configured the wan-interface of my FortiGate with vlan 4 as a subinterface. The code for this is displayed below.
config system interface
edit "vlan4"
set vdom "root"
set mode dhcp
config client-options
edit 1
set code 60
set type string
set value "IPTV_RG"
next
end
set distance 10
set alias "KPN iTV"
set dns-server-override disable
set interface "wan1"
set vlanid 4
next
endPlease mention the dhcp client-options part; this is mandatory because KPN will not give you an (valid) IP address when this client-option is not present in your DHCP-request. Option 60 needs to be present in your DHCP request, and the value must exact be IPTV_RG.
If everything is configured well, you should be able to get an IP address at this point. I got an 10.x.x.x address out of a /22 subnet. I also retrieve a DNS-server and a default gateway. To not distort the default-route which is currently active in my FortiGate for internet, I gave this default-gateway a higher distance of 10 (the default-gateway I retrieved for internet has a distance of 5). Another option is to disable the retrieval of the default-gateway at all on this interface.
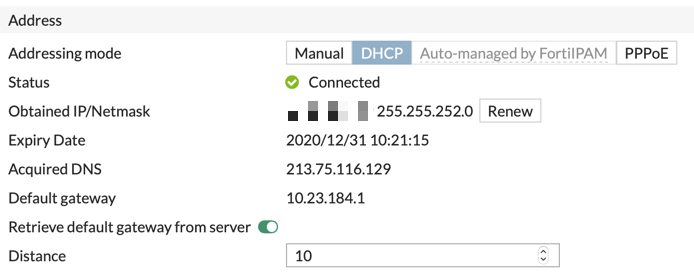
Step 2: create the necessary routing
What we now need to do, is to take care that the correct routing is applied for the subnet on which the iTV services reside on the KPN network. For KPN the iTV services are located in subnet 213.75.112.0/21, so we need to make sure that this subnet is routed correctly to the vlan 4 interface. For this to accomplish, we can do this with another DHCP client option on where KPN will return the routing-information back to the FortiGate. For now, I didn’t get this working. So I decided to configure another method, which was also very easy to implement.
As we have a dynamic address (DHCP) on the vlan 4 interface, I configured a static route where the next-hop address is dynamically determined through DHCP. See my example below.
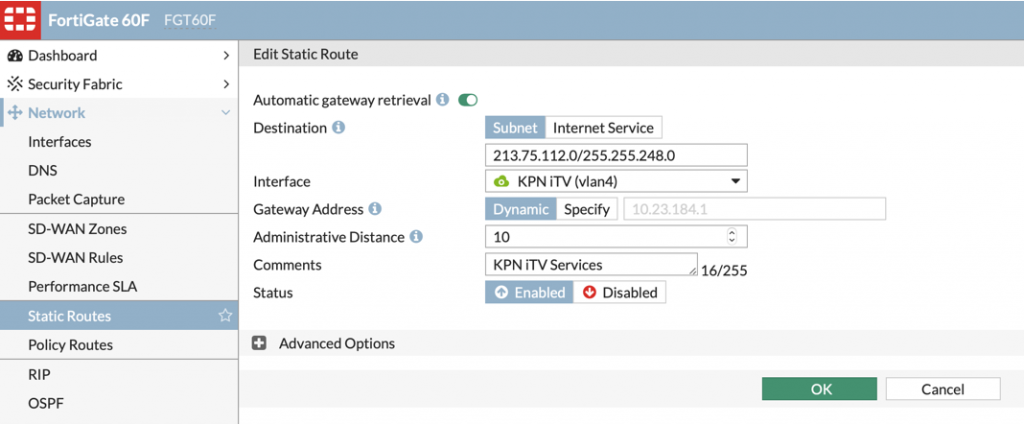
As you can see above, the next-hop is dynamically determined through DHCP.
Step 3: Configure the internal interface for the TV-receivers
In my home network, I created vlan 5 with subnet 10.5.1.0/24 for the network where my TV-receivers live. I configured my interface as follows:
config system interface
edit "vlan5"
set vdom "root"
set ip 10.5.1.1 255.255.255.0
set allowaccess ping
set alias "tv-receivers"
set interface "internal"
set vlanid 5
next
endI also enabled a DHCP server function in vlan 5, so that the TV-receivers get an IP address automatically. I specified the internet nameservers of KPN.
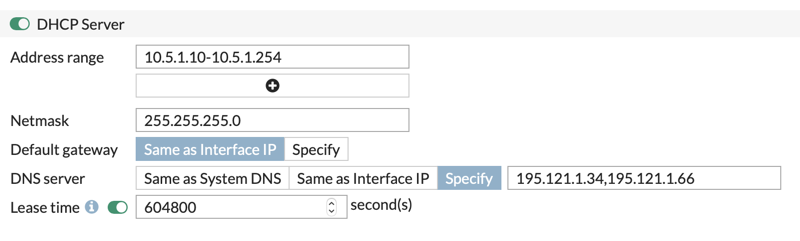
Step 4: Configure policy-rules
Because traffic for iTV is actually multicast traffic, we need to configure an inbound- and outbound multicast policy rule so that multicast-traffic is permitted to flow thorough the firewall. With this rules, source-natting is only required for outbound traffic; for inbound traffic, we can disable source-natting. My multicast rules are configured as follows. Mention the SNAT part of the rules.
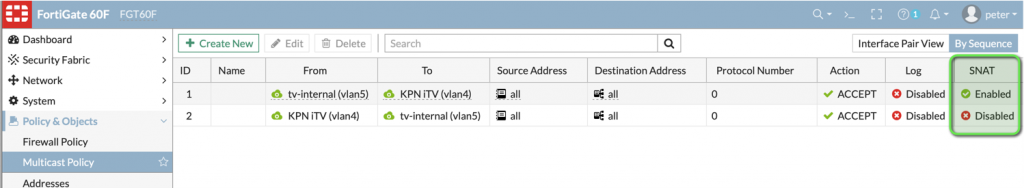
After configured the part above, you should be able to startup a receiver in the internal vlan. It gets an IP address, starts up, but it will get stuck on 85%…
Well, the problem with this is that the receiver also need some internet-access such as DNS, NTP and Netflix traffic. For this I configured a policy-rule, where I allow access to the internet.
After I configured these rules, the receiver starts successfully.
Step 5: Set some global-settings
At this point, you should be able to watch TV via your TV receiver. But it is possible that the screen is constantly “freezing”. This problem can easily be solved by entering the following command on the CLI.
config system settings
set multicast-ttl-notchange enableStep 6: Replay and Recordings
In my case, I noticed that replay and recordings did not work yet at this point. While recordings are actually an RTSP stream, I decided to disable the session-helper for RTSP traffic. For one or another reason, a FortiGate do not handle the RTSP traffic well.
In de default configuration, the RTSP session-helper has ID 6. So deleting this ID actually deletes the RTSP session-helper.
edit 6
set name rtsp
set protocol 6
set port 554
config system session-helper
FGT60F (session-helper) # delete 6
FGT60F (session-helper) # endThat’s all folks, everything should be working fine now! If you experience any issues, please drop a comment.
Hi Peter,
Great post, this is exactly what i was looking for.
Today i will receive a Fortigate 30E, I want to use this for my KPN internet. Sadly FortiOS 6.4 is not supported on this Fortigate, so no DHCP client option 60 for me…. You mentioned that you routed your multicast TV traffic through a dedicated microtik router, I want to achieve the same with an Ubiquiti Edgerouter Lite 3. Can you please tell me how you achieved this.
Thanks.
Marco
Never mind, I tried to configure the internet connection today and even this is not possible on a 30E. The first step to set the mtu size to 1514 failed, it seems the 30E doesn’t support a mtu size larger the 1500. So this one can go into the bin.
regards,
Marco
Use ‘set tcp-mss-sender 1440’ on the outbound IPTV firewall policy to slightly lower the maximum segment size for the data stream.
yes you can, but this setting applies only to TCP traffic, not to UDP. And if you want to make things right, I prefer to make it possible to support 1500 bytes. In fact, this makes an MTU of 1472 possible for your network-hosts (1500-28 bytes of overhead). To check the MTU size (end-to-end), the following URL can be used: http://www.letmecheck.it/mtu-test.php
Held, dank voor deze handleiding!
Hi Peter,
thanks for your nice manual. The only thing is that it’s still stuck at 85%. What can I do to find out what’s wrong?
Regards Stefan
Ps Using Fortigate 60E and why is the receivers VLANID=5? Can I put a port of the fortigate at vlan5?
After a while of trying and testing I managed to get this setup (with my own twist on it) working. I can say this also works on a fortigate 60E with firmware 7.0.5.
To make things a little easier for other peaple who want this:
in this configuration an extra static route has to be configured, I think this has been adjusted in the meantime:
“10.59.184.0/21 interface: kpn ITV (vlan4) with dynamic gateway” Source: “https://gathering.tweakers.net/forum/list_messages/2087576”
Further in step 4 Peter is using “multicast policy” option under “policy & Objects” But with an Fortigate without config this is not there. If you go first to “system -> Feature Visibility -> and enable ‘Multicast policy'” you will see this option.
Further under building ethernet (part 1 of this post) you have to add some commands to make it work:
edit “internet”
set vdom root
set alias “vlan6”
set estimated-upstream-bandwidth 200000
set estimated-downstream-bandwidth 200000
set role wan
set interface “wan1”
set snmp-index 69
set mtu-override enable
set mtu 1506
set vlanid 6
next
end
config system interface
edit “pppoe1”
set mode pppoe
set vdom root
set allowaccess ping
set type tunnel
set estimated-upstream-bandwidth 200000
set estimated-downstream-bandwidth 200000
config ipv6
set ip6-mode dhcp
set ip6-allowaccess ping
set dhcp6-prefix-delegation enable
end
set interface “internet”
next
end
And for some reason the above “set type tunnel” wont work. But if you make the pppoe in the GUI and edit it afterwards in the CLI you can see that is has added the “set type tunnel”. (Dont ask me why.)
And I would disable Ping from my pppoe session, but that is just my opinion.
Thanks Peter for this amazing post 😉
Hi Peter,
I’m having issues with playing recordings and replay. They stream but every few minutes it freezes a few seconds and then continuous. I have disabled all security profiles on the policy and disabled the RTSP session helper. Live TV, Netflix or other apps on the ITV box play flawlessly.
I have a 60E with latest firmware 7.2.1
Any toughs about this?
Just to give some people some information in case they are trying this and not getting IPtv to rewind:
I dont get this setup working with the new IPtv box from kpn (4k kind with name: VIP5202 manufacture date 2022-05)
What currently does work with this new box:
-Watching normal TV (I got it to work to let it connect and configure itself with the experiabox between it. and then without powering off the device and plugging it into my fortigate it will work)
What does not work with the new box:
-Playing back video (like pressing the back button to rewind the bit you just saw)
-Watching back an show via the guide.
-Booting the device with the fortigate between it (Awake from standby does work.)
I could not yet figure out what the problem is exactly. I get the feeling the new box is trying to connect to an ip range that we haven’t given a static route yet.
I need to wireshark to investigate and or just use the fortigate to check. (Did not do that just yet)
Foult code (in dutch)
”
Het progamma kan niet worden afgespeeld door een probleem in het netwerk
Probeer het later nog eens.
(STB-zap-01 – video niet gevonden)
”
I have this setup running from April 2, 2022 to now with the old box without any problems (1080P VIP2952 manufacture date 2014)
the old box I can just totaly power off and reboot without any issues. And that one will rewind etc.
It can totaly be that I’m the only one here with this problem. But I wanted to at least post this before people are pulling their hair out in frustration because they can’t get it to work 🙂
If you reply to this post first check your VIP number of the box you got, and post it with it (So we can make a list or someting of boxes that do work and don’t.)
If im behind the solution im going to post it again.
As promised I tried some things (finally had time to do that)
The problem was that I made the subnet for the IPTV too small (255.255.255.252). It should have been good because you have 2 addresses 1 for the new 1 for the old. But for some reason (still not sure what exactly) it just didn’t work.
Changed that to a /24 (255.255.255.0) it’s too big but it’s fine, everything works as it should now.
Vraagje nog over internet username en password. In mijn Huidige Experiabox is dit niet te copy en paste in de fortigate.
Ik neem aan dit ik dit via dhcp in de forti moet verkrijgen ? Want het passwoord weet ik niet. Via de KPN servicetool is de username wel op te vragen en het passwoord dient men zelf in te vullen. Klopt dat ?
does someone have an idea to do the same thing with the austrian isp a1? here it is also vlan 4 but I dont have a clue which other settings e.g dhcp options I need to use?!